Cyber criminals keep creatively upping their game and this new phishing attack is proof of that. A new worm phishing […]
Currently browsing: Blog
Major Data Breach of Government Computers
The National Informatics Center (NIC) and the Ministy of Electronics & Information Technology (MeitY) suffered a data breach in early […]
Look out for Covid-19 Related Cyber Scams
While regulations have lifted the restrictions of strict lockdowns, common sense and the growing number of Covid-19 cases suggest otherwise. […]
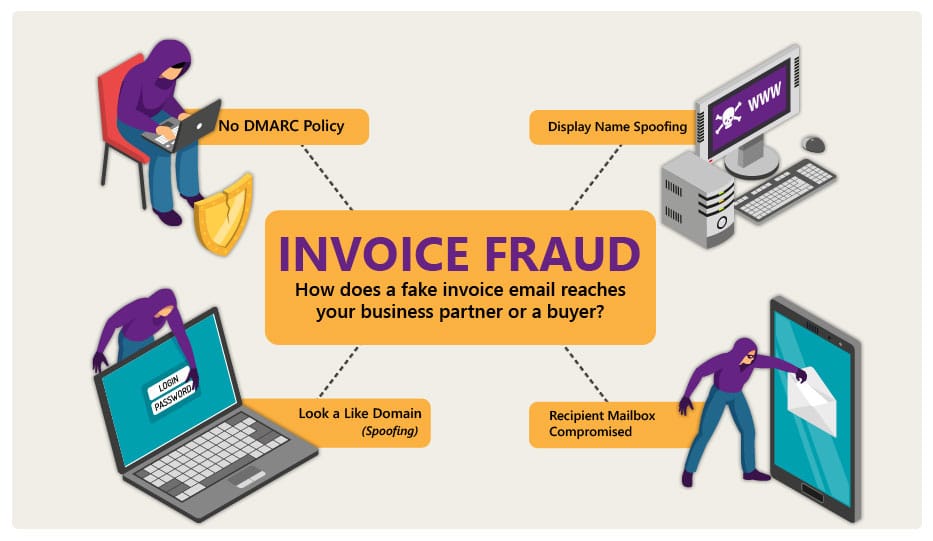
Email Invoice Fraud Prevention – A Concise Guide
Business owners are now growing increasingly aware of cyber security concerns hanging over their heads like a dark cloud. That […]
Logix is a Microsoft Gold Partner in India
What are our offerings as a Microsoft Gold Partner? For some time now, the corporate sector has been all about […]
Nykaa Email Spoofing Case
Nykaa Loses 62Lakh To Cyber Fraud Most of the times, it is the individual shoppers and customers who are at […]
4 Ways Fraud Invoices Can Affect Your Business
Why Worry About Fraud Invoices? Fraud Invoices could victimize any business. Invoice fraud is a type of attack in which […]
4 Factors To Consider When Choosing Between Email Archival And Deletion
Is Email Archival Better than Email Deletion? Every business relies on email correspondence to some level. But as the volume […]