Case Specifics A private company based in Pune recently suffered from a server hack. The hackers, who remain as of […]
Currently browsing: Blog
Malwarebytes Hacked by The Same Group Behind SolarWinds Security Breach
Cyber security firm themselves are lucrative targets for hackers. It is a matter of pride for them; their way of […]
Common Cyber Attacks You Should Know
It is true that most common cyber attacks leverage gaps in technical devices or technological aspects a business uses, to […]
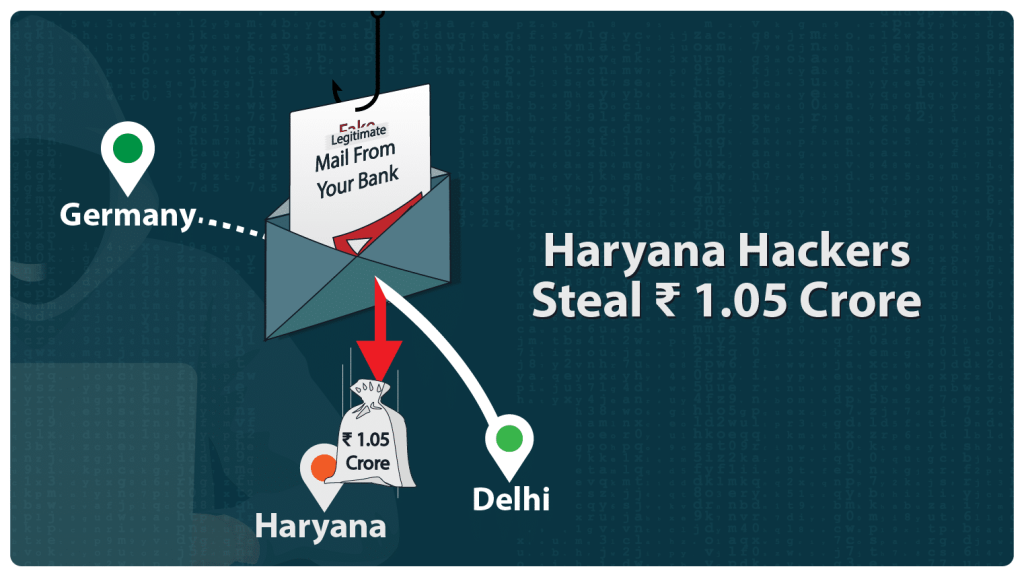
Haryana Hackers Steal INR 1 Crore
Haryana hackers defrauded ISGEC Heavy Engineering company and nicked an amount of INR 1.05 crore. These hackers intruded upon ISGEC’s […]
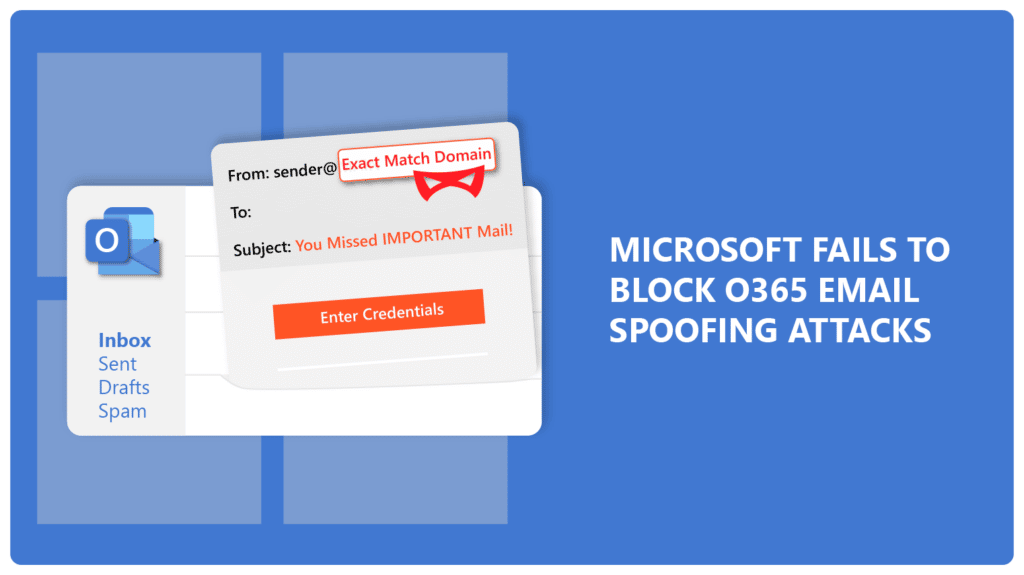
Microsoft Fails to Block O365 Email Spoofing Attacks
Microsoft is under the gun again for cyber fraud. 200 million+ users are at a risk of O365 email spoofing […]
What are the types of Network Security Devices?
In a previous blog, we explored various concepts associated with network security. If you haven’t already, we highly recommend reading […]
Understanding Network Security
Communication to and from devices essentially happens via networks. That network can be private (within an organization) or public (via […]
Features of Cisco Email ATP
Cisco provides one of the strongest email security solutions available today. In our blog on Cisco IronPort offering, we discussed […]
Your Guide To Prevent Phishing – Know How Hackers Think
Cyber criminals are getting creative with their ways and organizations have to lookout for new ways to prevent phishing attacks. […]
Pune-based Engineering Company Duped Out Of 50 lakhs
It’s cyber fraud cases like these that remind us of the gravity of cyber security. A Pune-based engineering company, with […]