An update on the data protection law December brought in some good news as a hopeful end to 2019. With […]
Currently browsing: Blog
Fake Greta Thunberg Email Spreads A Dangerous Malware
Fake Greta Thunberg Emails Used to Ensnare New Victims Stories of brave individuals fighting for the overall betterment of our […]
DNS Protection
Protect Your DNS – How & Why? DNS or Domain Naming System is a computer server which accommodates public IP […]
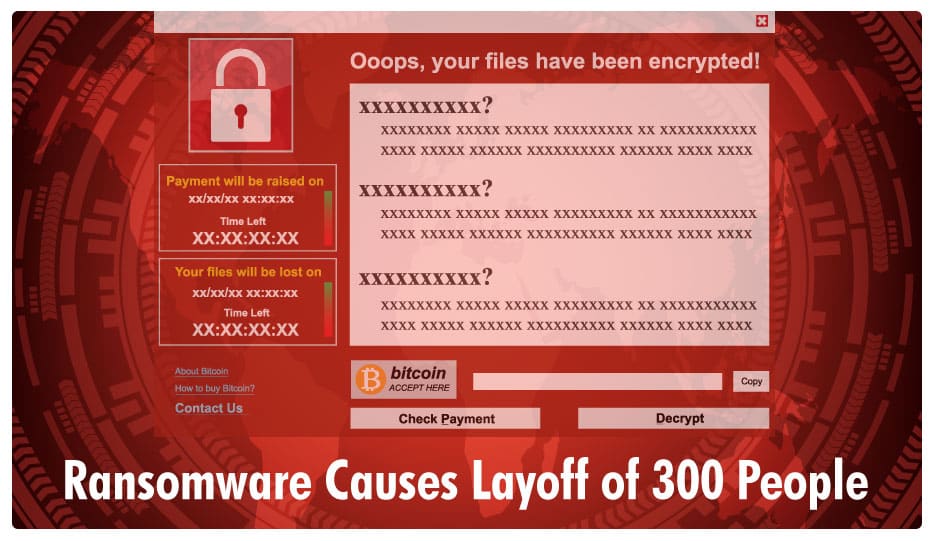
Ransomware Causes 300 People To Lose Their Jobs
Ransomware Forces An Organization To Let Go Of 300 Employees Ransomware has been known to cause a lot of monetary […]
Emotet botnet malware hidden within fake Christmas party invites
Beware: Your Christmas party emails could be infected with malware Nobody likes downers when it comes to the holiday spirit. […]
Microsoft Report on Cleverest Phishing Tactics
Microsoft Reports on the Cleverest Phishing Tactics of 2019 While for individuals it is frustrating — and threatening — how […]
Best Practices For Online Security
Security Practices for Your Business — How many can you check off your list? When it comes to online security, […]
Ukraine Targeted by a Russian APT Hacker Team
Russian APT Hacker Team Strikes Out The Military and the Government are under the gun once again. The country of […]
Defence Ministry Targeted For Phishing
Warning Issued for Defence Personnel The defence ministry has issued an emergency warning to all defence personnel not to open […]
Most Likely Phishing Targets
Organizations Most at Risk of Phishing Phishing is a rapidly damaging cybercrime that has targeted a wide variety of domains […]