A slow-burn cyber breach has been transpiring since January, only recently coming to public attention. Due to Microsoft Exchange server […]
All posts by LES Support at Logix
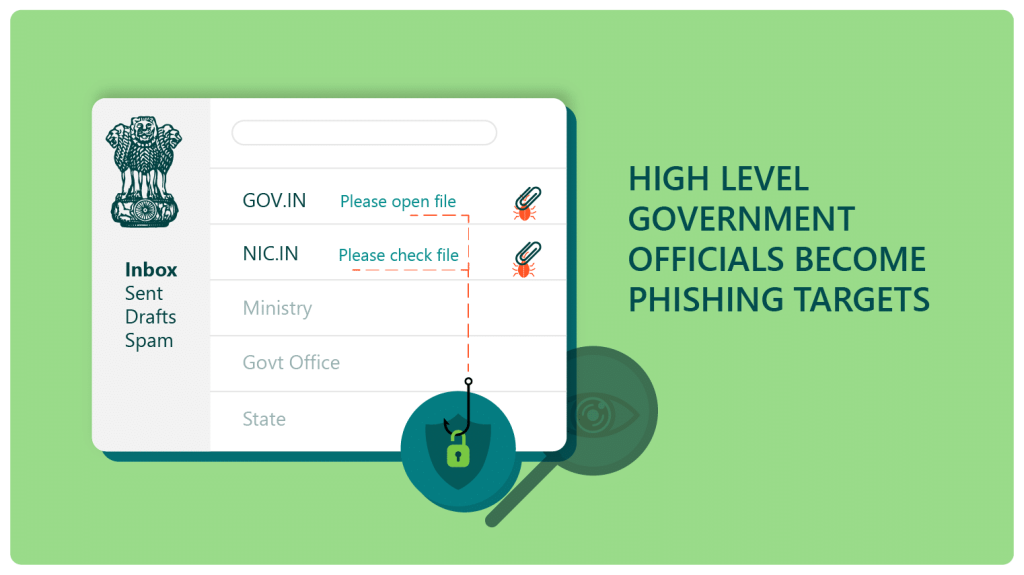
Hackers Target Government Officials Through Rogue Email ID
Several officials in the government were targeted for phishing through a rogue email ID. These government officials were spread out […]
Getting a bonus is always good… unless it’s an advanced Bazar Trojan in disguise
Security researchers have found a deadly variant of a Bazar Trojan that grabs control of your machine and cedes it […]
Hosting Provider Phishing Scam
Cyber criminals will often use scare tactics to prod their victims into interacting with their phishing links and malicious programs. […]
What is Cloud Security & Why Do You Need A Cloud Firewall?
The advent of cloud computing gave rise to hyper connectivity and constant availability. Data could not only be stored on […]
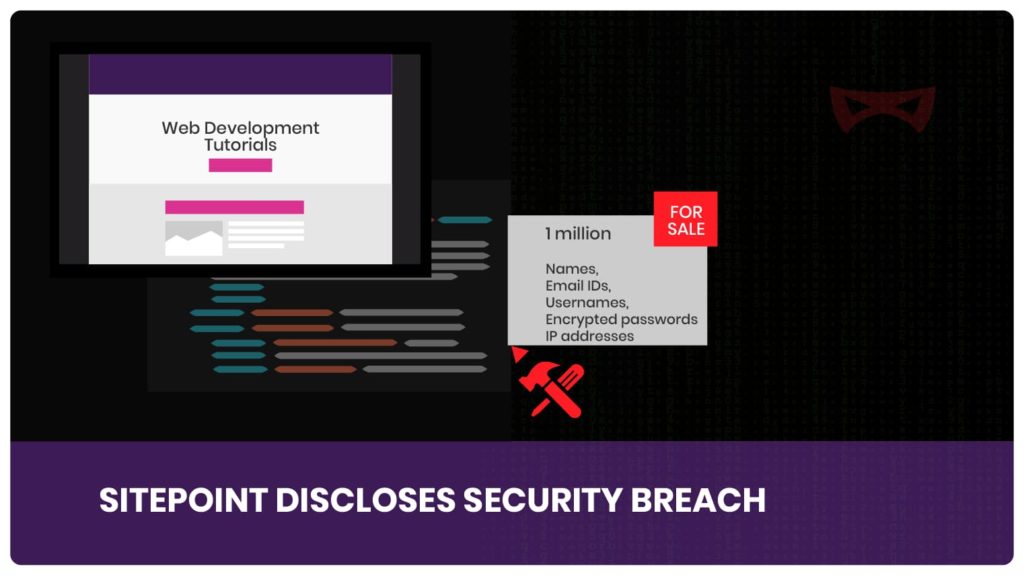
SitePoint Security Breach
SitePoint is an online portal which provides some great tutorials on web development. It recently went through a security breach […]
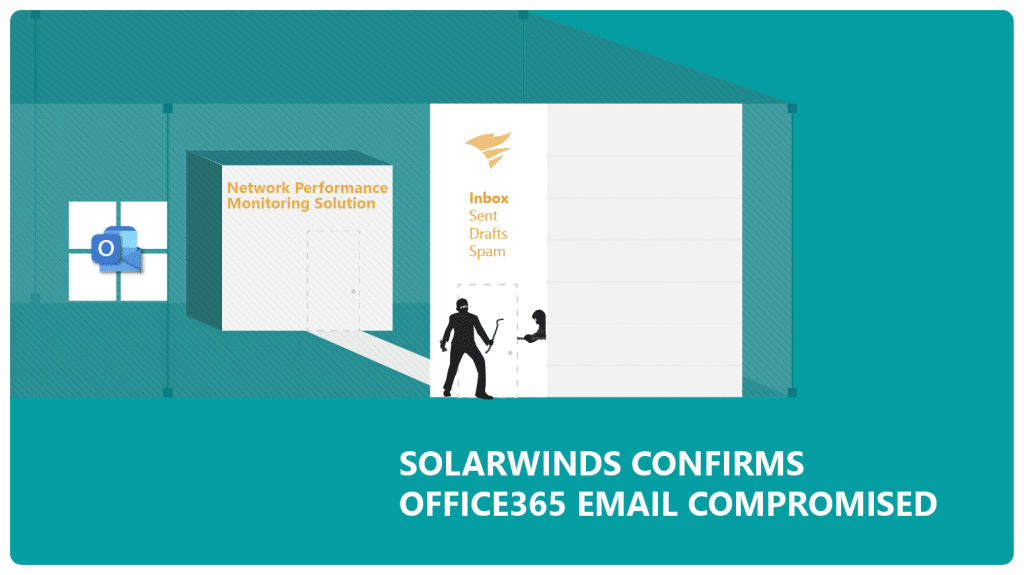
Office365 Email Compromise – SolarWinds Faces Security Breach
SolarWinds, an IT services company, recently faced issue with their email security. Sudhakar Ramakrishna, CEO SolarWinds, suspects a zero-day vulnerability […]
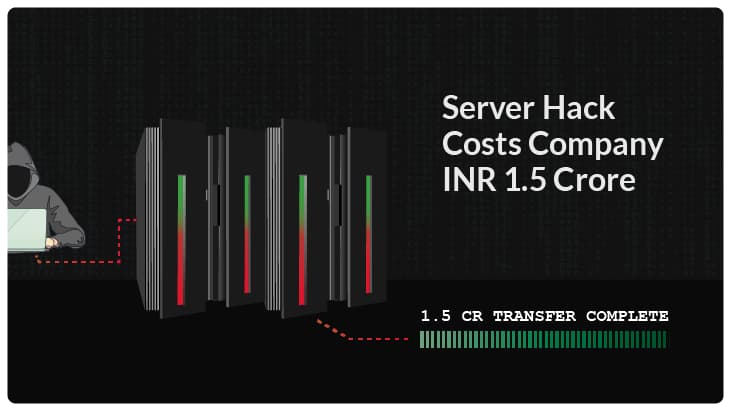
Server Hack Costs 1.5 Crore in Losses
Case Specifics A private company based in Pune recently suffered from a server hack. The hackers, who remain as of […]
Malwarebytes Hacked by The Same Group Behind SolarWinds Security Breach
Cyber security firm themselves are lucrative targets for hackers. It is a matter of pride for them; their way of […]
Common Cyber Attacks You Should Know
It is true that most common cyber attacks leverage gaps in technical devices or technological aspects a business uses, to […]