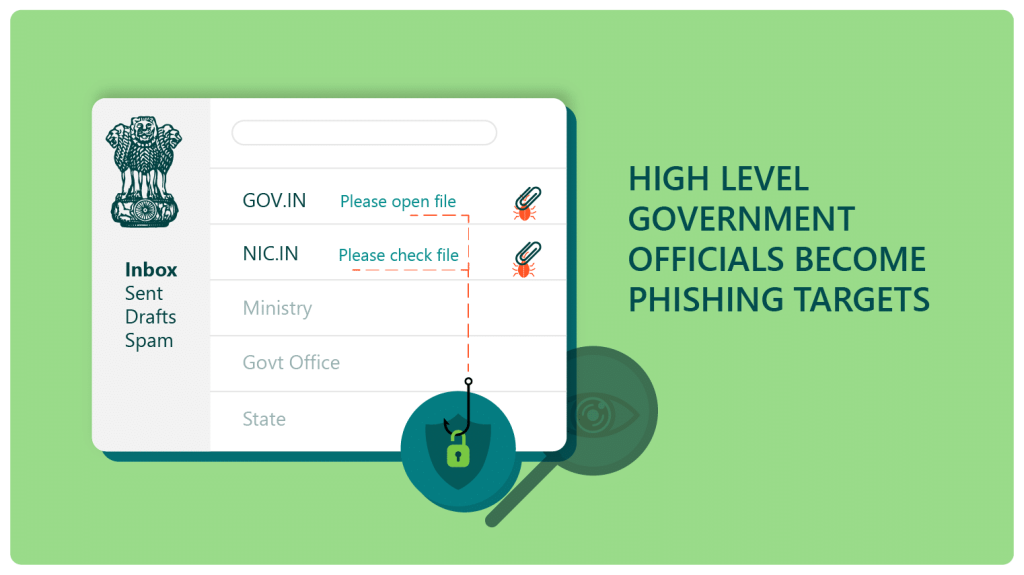
Several officials in the government were targeted for phishing through a rogue email ID. These government officials were spread out over departmental ministries, like the Ministry of Defence and the Ministry of External Affairs. The rogue email ID belonged to a compromised governmental domain. The NIC (National Informatics Centre) soon intervened, but couldn’t be sure whether any of the sensitive governmental machines were compromised by the phishing attack. “The attacks highlight the constant threat from hackers, and the need for better authentication protocols,” say the experts who investigated the phishing attempts.
Who were the targets of the rogue email ID?
The governmental agencies have their own mailing lists, at least 3 of which were targeted for phishing. The phishing emails were sent along with an attachment, the downloading of which would trigger the installation of malware on these information-rich computers. The malware was rigged to create backdoor access to these machines, practically leaving an inviting for spying or data theft.
Which compromised domains were misused?
Two emails were sent from @gov.in and @nic.in email addresses. These domains were used to make the government victims falsely believe that these emails originated from a valid source.
“The phishing emails were sent on February 10 to various officials across the ministries of external affairs and defence and others, with attached documents asking the recipients to click on the files. Soon after, NIC alerted the concerned branches of the potential security breach and notified all officials across ministries of the compromised emails,” said an official related to the case.
The NIC runs the mailing service for the government, and allocates these two domains itself (@gov.in and @nic.in). The Union and State government, along with state-owned enterprises / SOEs (for e.g., Bharat Petroleum or the State Bank of India) can use these domains for their websites and their email IDs. But this allocation happens only after a rigorous verification system, overseen by individual NIC authorities dedicated to particular ministries or SOEs.
A cybersecurity official who has previously worked on cyber fraud cases for the government shed light on how these rogue email ID attacks have been carried out in the past.
“Dormant accounts of NIC were used to launch attacks against several top government officials at the time,” the official said, referring to a mass phishing campaign that had been launched back in 2008-2009. In that campaign, phishing emails from a rogue email ID were delivered to at least 450 top governmental officials, including accounts used even by the then Prime Minister’s Office, the NSA, and the external affairs ministry.
The nature of the phishing attack
The same official who remarked about the earlier phishing attack, also analysed this attempt. He believes this technique was primitive, but might have only been used so the hackers could have one foot in the door. Later, they would’ve moved on to more advanced and sneakier techniques, steadily widening their net until they could spy across governmental ministries.
What was especially noteworthy about this attack was the fact that the hackers could get their hands on NIC and GOV email domains, which are not handed out lightly to just about anyone.
“Having access to a privileged email domain is always a great vector from an attacker’s perspective because this way, they are able to reach directly into the inbox of their targets and defeat filters that usually flag suspicious messages. This way, they can also chain attack, compromising one official after the other,” – Yash Kadakia, CTO, Security Brigade, a cybersecurity firm within the employ of the government.
Because these particular domains are always used to send emails to mailing lists, the hackers could launch phishing attempts even if they did not know the exact email ID of a particular minister. This allowed the hackers to tailor their attacks to elicit an emotional / spontaneous response from the kind of people working in that particular department.
We will leave you with a simple yet insightful comment from Mr. Kadakia: “An OTP (one-time password) for sign-in is one easy way to stop such attacks even if basic login credentials are compromised.” It’s a cue for the online community of businesses to employ multi-factor authentication at once. For more resources on cyber security, visit our blog.